Vba2Graph - Generate call graphs from VBA code, for easier analysis of malicious documents.
Vba2Graph
A tool for security researchers, who waste their time analyzing malicious Office macros.
Generates a VBA call graph, with potential malicious keywords highlighted.
Allows for quick analysis of malicous macros, and easy understanding of the execution flow.
Features
- Keyword highlighting
- VBA Properties support
- External function declarion support
- Tricky macros with “_Change” execution triggers
- Fancy color schemes!
Pros
✓ Pretty fast
✓ Works well on most malicious macros observed in the wild
Cons
✗ Static (dynamicaly resolved calls would not be recognized)
Examples
Example 1:
Trickbot downloader - utilizes object Resize event as initial trigger, followed by TextBox_Change triggers.
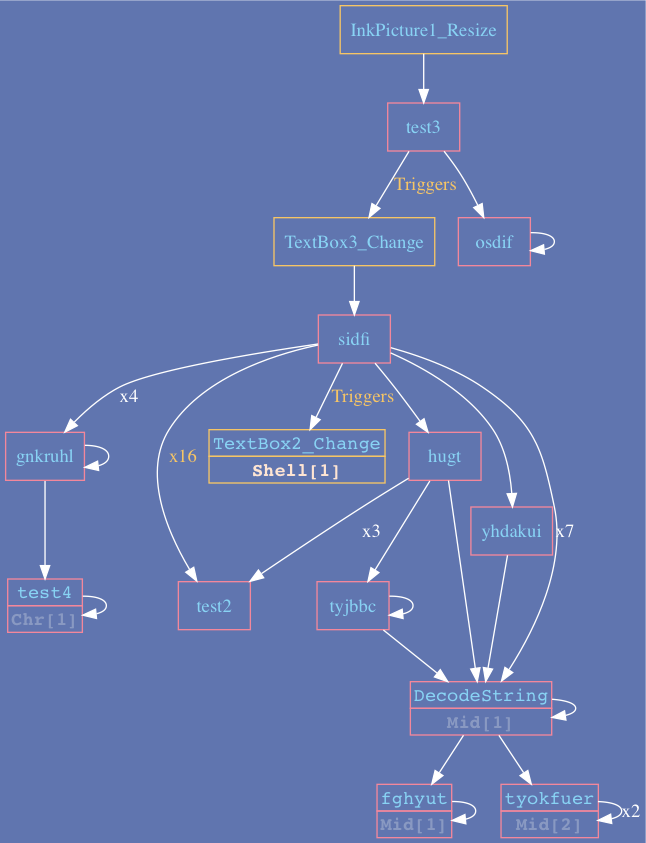
Example 2:
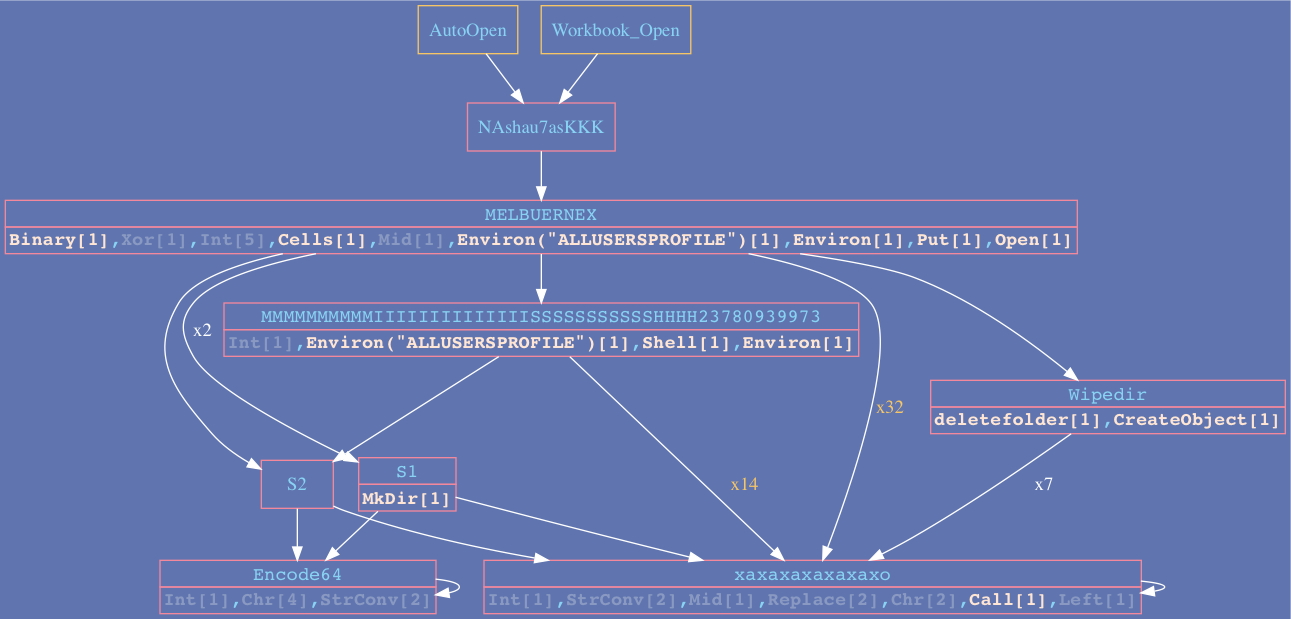
Check out the Examples folder for more cases.
Installation
Install oletools:
https://github.com/decalage2/oletools/wiki/Install
Install Python Requirements
pip3 install -r requirements.txt
Install Graphviz
Windows
Install Graphviz:
https://graphviz.gitlab.io/download/#windows
Add “dot.exe” to PATH env variable or just:
set PATH=%PATH%;C:\Program Files (x86)\Graphviz2.38\bin
Mac
brew install graphviz
Ubuntu
sudo apt-get install graphviz
Arch
sudo pacman -S graphviz
Usage
usage: vba2graph.py [-h] [-o OUTPUT] [-c {0,1,2,3}] (-i INPUT | -f FILE)
optional arguments:
-h, --help show this help message and exit
-o OUTPUT, --output OUTPUT
output folder (default: "output")
-c {0,1,2,3}, --colors {0,1,2,3}
color scheme number [0, 1, 2, 3] (default: 0 - B&W)
-i INPUT, --input INPUT
olevba generated file or .bas file
-f FILE, --file FILE Office file with macros
Usage Examples (All Platforms)
Please note that a Python 2 release is availiable in the Releases section, but is no longer supported.
# Generate call graph directly from an Office file with macros [tnx @doomedraven]
python3 vba2graph.py -f malicious.doc -c 2
# Generate vba code using olevba then pipe it to vba2graph
olevba3 malicious.doc | python3 vba2graph.py -c 1
# Generate call graph from VBA code
python3 vba2graph.py -i vba_code.bas -o output_folder
Output
You’ll get 4 folders in your output folder:
- png: the actual graph image you are looking for
- svg: same graph image, just in vector graphics
- dot: the dot file which was used to create the graph image
- bas: the VBA functions code that was recognized by the script (for debugging)
Batch Processing
Mac/Linux:
batch.sh script file is attached for running olevba and vba2graph on an input folder of malicious docs.
Deletes output dir. use with caution.
License
The code in this project is licensed under the EPL-2.0 License.
This project is utilizing the following third-party open-source tools and libraries.
Please note their respective licenses.